Apple Releases macOS High Sierra Security Update to Fix Huge Root Password Vulnerability
Apple released a High Sierra Security Update today to fix a critical vulnerability which allowed anyone without a password to access to the root superuser account with a blank password. This vulnerability affects any Mac running macOS High Sierra version 10.13.1. The High Sierra security update, termed Security Update 2017-001 will be rolled out via the Mac App Store on your High Sierra system.
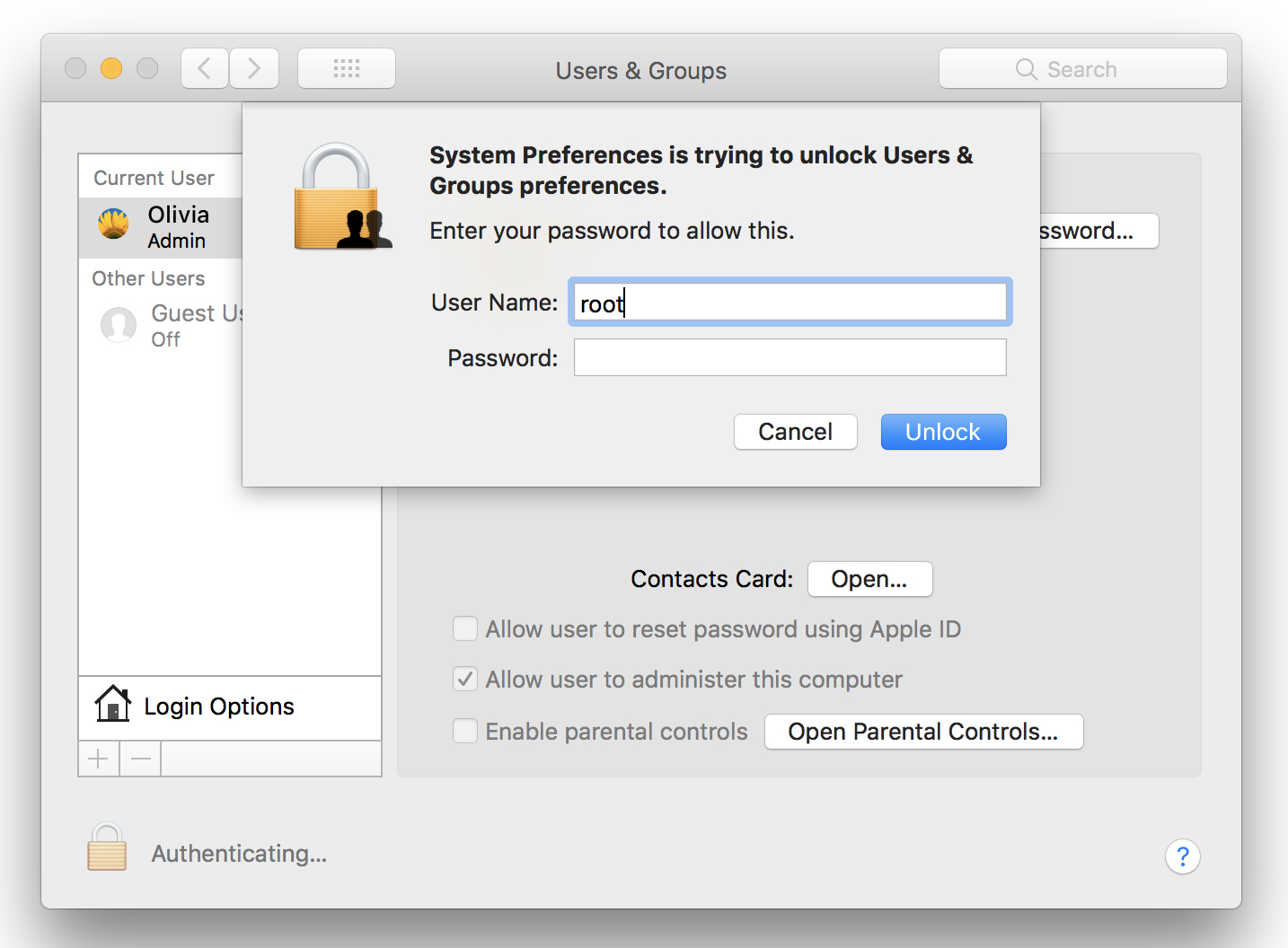
The major security bug garnered attention after it was tweeted by developer Lemi Ergin. It is reported by many online magazines due to the critical nature of the bug. The bug allows anyone to gain administrative rights by simply entering the username “root” followed by a blank password in System Preferences > Users & Groups.
The High Sierra Security Update should be installed by all users running macOS High Sierra as soon as possible. In lieu of the critical nature of the big, Apple will be pushing out the update automatically to be installed on all Macs running macOS High Sierra 10.13.1.
The update was installed automatically without our intervention on one of our own iMac running MacOS High Sierra 10.13.1. On our other iMac Retina 5K 27inch 2017, we were unable to see the High Sierra security update at the Mac App Store during the time of writing. If you are unable to see the update on your Mac App Store, the security update can be downloaded here.
When you install Security Update 2017-001 on your Mac, the build number of macOS will be changed to 17B1002. The build number of your MacOS High Sierra can be found by clicking the Apple menu in the top left corner of your screen followed by choosing “About This Mac”. The version of your operating system appears beneath “macOS” or “OS X” in the window that opens. If you need to know the build, click the version.
Apple has since apologised for the major bug in a statement issued online magazines. The statement is reprinted here:
Security is a top priority for every Apple product, and regrettably we stumbled with this release of macOS.
When our security engineers became aware of the issue Tuesday afternoon, we immediately began working on an update that closes the security hole. This morning, as of 8 a.m., the update is available for download, and starting later today it will be automatically installed on all systems running the latest version (10.13.1) of macOS High Sierra.
We greatly regret this error and we apologize to all Mac users, both for releasing with this vulnerability and for the concern it has caused. Our customers deserve better. We are auditing our development processes to help prevent this from happening again.
Let us know if you are facing other MacOS High Sierra update issues. We are happy to help.
